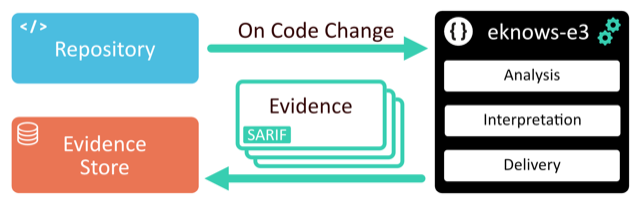
eknows-e3 (eknows evidence extractor) is part of the evidence gathering tools which are being developed in EMERALD and supports the assessment of security and compliance of a cloud application’s source code. It extracts evidence required for later assessments, such as identifying used transport layer protocols and cipher suites. The static code analysis platform eknows [1] [2] is the basis for the extractor and provides the foundation for the extraction capabilities.
eknows-e3 supports the analysis of Maven projects which are written in Java. It identifies used security providers and extracts evidence regarding the implemented SSL/TLS setup. Furthermore, it extracts evidence regarding vulnerabilities, which appear in the dependency tree of the given project. The evidence is exported in the EMERALD evidence format and sent to the Evidence Store. The evidence is also supplemented with additional information in the standardized SARIF [3] format, which will enable future reporting.
For convenient deployment, eknows-e3 can be integrated into existing GitLab CI/CD pipelines by including a ready-to-use component. By this, the latest version of the code is always being analyzed and any deviations from standards and guidelines can be detected as soon as possible.
eknows-e3 is continuously developed and extended. Currently, the following two extensions to two new domains are in development: The extraction of evidence from the git commit history of a git repository, and from pull requests and issues/tickets. Both will enable the verification of adherence to development guidelines. In addition, the integration possibilities of LLMs to enhance static code analysis tasks are being explored.
More information about eknows-e3 can be found in our latest deliverable D2.3 [4] and the latest public version of eknows-e3 is available on our GitLab repository [5].
[1] https://doi.org/10.1109/MS.2024.3359458
[2] https://www.scch.at/software-science/projekte/detail/eKnows
[3] https://docs.oasis-open.org/sarif/sarif/v2.1.0/sarif-v2.1.0.html
[4] https://www.emerald-he.eu/wp-content/uploads/2025/11/EMERALD_D2.3_Source-Evidence-Extractor-v2_v1.0.pdf
[5] https://git.code.tecnalia.dev/emerald/public/components/eknows